

Indirector: High-Precision Branch Target Injection Attacks Exploiting the Indirect Branch Predictor (Distinguished Paper Award Winner!)
USENIX Security Symposium, August 2024.
Luyi Li*, Hosein Yavarzadeh*, Dean Tullsen
*Equal contribution joint first authors
[ Paper | Code | bibtex | Video | Slides]
This paper introduces novel high-precision Branch Target Injection (BTI) attacks, leveraging the intricate structures of the Indirect Branch Predictor (IBP) and the Branch Target Buffer (BTB) in high-end Intel CPUs (Raptor Lake and Alder Lake).
It presents, for the first time, a comprehensive picture of the IBP and the BTB within the most recent Intel processors, revealing their size, structure, and the precise functions governing index and tag hashing.
Additionally, this study reveals new details into the inner workings of Intel's hardware defenses, such as IBPB, IBRS, and STIBP, including previously unknown holes in their coverage.
Leveraging insights from reverse engineering efforts, this research develops highly precise Branch Target Injection (BTI) attacks to breach security boundaries across diverse scenarios, including cross-process and cross-privilege scenarios and uses the IBP and the BTB to break Address Space Layout Randomization (ASLR).
Branch Target Injection (BTI) attacks exploit the branch prediction hardware in modern CPUs to redirect the control flow of a program. These attacks have been the subject of extensive research since the discovery of Spectre and Meltdown in 2018. However, existing studies have primarily focused on the Branch Target Buffer (BTB) and Return Stack Buffer (RSB) while overlooking the Indirect Branch Predictor (IBP). The IBP is a critical component of the branch prediction unit that predicts the target address of indirect branches. By analyzing the IBP, we uncover new attack vectors that can bypass existing defenses and compromise the security of modern CPUs.
The Indirect Branch Predictor (IBP) is a hardware component in modern CPUs that predicts the target addresses of indirect branches. Indirect branches are control flow instructions whose target address is computed at runtime, making them challenging to predict accurately. The IBP uses a combination of global history and branch address to predict the target address of indirect branches. By analyzing the structure and operation of the IBP, we identify vulnerabilities that can be exploited to launch precise Branch Target Injection (BTI) attacks.
In this study, we reverse engineer the structure of the IBP in high-end Intel CPUs for the first time and provide a detailed analysis of its size, structure, and prediction mechanisms. Here, we present the overall structure of the IBP, however the details are omitted for the sake of brevity. For more information, please refer to the full paper.
In order to reverse engineer the IBP, we developed carefeully crafted microbenchmarks to probe the behavior of the IBP and extract its internal state. We used performance counters to measure the number of indirect branch predictions and mispredictions, which allowed us to infer the structure of the IBP. All the experiments can be found in the Indirector Artifact Repository.
We found that the IBP in the modern Intel CPUs features a set-associative structure with three tables, each being 2-way set associative indexed with different global history lengths (Similar to ITTAGE).
The following figure illustrates the structure of the IBP in modern Intel CPUs:
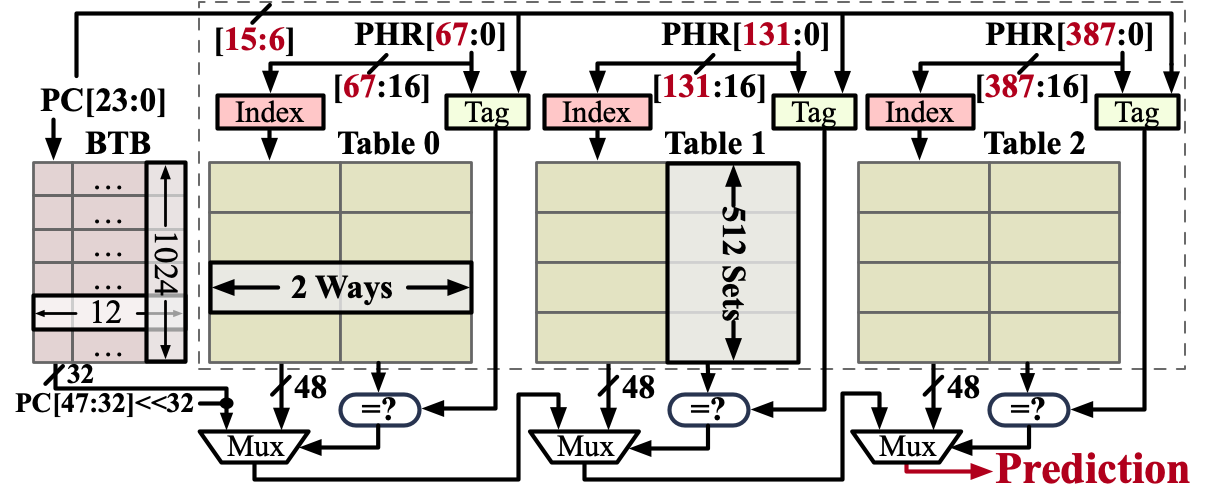
As shown in the figure, the IBP consists of three tables: Table 0 uses 68 lower bits of the global history (PHR), Table 1 uses 132 lower bits of the PHR, and Table 2 uses the entire 388-bit PHR.
Each table is 2-way set associative with 512 entries per way. The IBP uses a hash function to compute the index and the tag into each table based on the PHR and the branch instruction address (PC).
We found the exact index and tag hashing functions used by the IBP in modern Intel CPUs, which are crucial for launching precise BTI attacks. By exploiting these vulnerabilities, an attacker can manipulate the prediction of indirect branches and precisely redirect the control flow of a program to a malicious target address.
The overall index and tag hash functions for the tables are similar to folded PHR, with the index folded into 9 bits and the tag folded into 11 bits. For detailed information on the exact hash functions, please refer to the paper.
Building upon our new, much deeper understanding of the IBP structure, we propose iBranch Locator, an efficient and high-resolution tool to locate any indirect branch within the IBP, without the need to know any prior history information before the branch. In this tool, the locating process is divided into two steps: first finding the IBP index and then searching for tag aliasing.
The first step is to identify the IBP set where the victim's indirect branch is located, which involves extracting the index of the victim entry. To determine the set used by the victim branch, the iBranch Index Locator performs an associativity test during the victim's execution using an eviction-based contention technique. Locating the victim entry is challenging as it requires both the index and the tag, with the tag hash function differing from the index hash function. Therefore, the second step of iBranch Locator is to search for tag aliasing. Although a brute force search for the 11 bits by controlling the PHR is possible, it demands significant effort to create both index and tag aliasing simultaneously.
In our reverse engineering efforts, we discovered that 10 bits of the tag are directly XORed with the PC bits, which significantly simplifies the search for tag aliasing. For the 11th bit, only specific bits of the PHR are required to control the tag. Overall, iBranch Locator can locate any victim IBP entry with significantly less effort than brute force search, compared to prior BHI attack.
Utilizing this tool, two injection attacks can be easily mounted with precision, which will be presented in the following section.
To mitigate the risks posed by Indirector attacks, we recommend the following countermeasures:
1. Using IBPB more aggressively: To the best of our understanding, Linux opts to automatically activate the IBPB during context switches between different users.
The default policy in the latest Linux version, termed IBPB: conditional, only activates IBPB during transitions to SECCOMP mode or tasks with restricted indirect branches in the kernel. Consequently, IBPB activation is infrequent in both user and kernel spaces due to the significant performance overhead (up to 50%).
It is not a viable mitigation for frequent domain crossings (browsers, sandboxes, and even kernel/user) - plus the fact that the OS does not use it in the most frequent domain transitions by default.
2. Secure BPU Design: Our study highlights that Intel has already integrated new fields such as Core-ID and Privilege Level into their recent Indirect Branch Predictor (IBP) design. This inclusion aims to prevent aliasing between indirect branches originating from different SMT cores and different privilege levels, respectively.
However, this still leaves potential attack surfaces within the same-core and/or same-privilege scenarios.
For future BPU designs, a more complicated tag should be considered to provide more fine-grained isolation across security domain
We communicated the security findings outlined in the paper to Intel in February 2024. Intel has informed other affected hardware/software vendors about the issues.
Intel's Security Announcement can be found here.
@inproceedings{Li2024Indirector,
title = {{Indirector}: High-Precision Branch Target Injection Attacks Exploiting the Indirect Branch Predictor},
author = {Luyi Li, Hosein Yavarzadeh and Dean Tullsen},
booktitle = {33rd {USENIX} Security Symposium ({USENIX} Security 24)},
year = {2024}
}
If you have any questions, please do not hesitate to reach out to us at hyavarzadeh@ucsd.edu and lul014@ucsd.edu.